
Panda Adaptive Defense 360
Find the Answer, Solve the Problem
Panda Security is now a part of WatchGuard Technologies, please visit our WatchGuard Technologies website to learn more about this product!
Overview:
Complete endpoint defense integrating protection, detection, response and remediation for all types of threats in a single solution.
Panda Adaptive Defense 360 is the first and only cyber-security solution to combine the most effective traditional antivirus and the latest advanced protection technology with the ability to classify all running processes.
Adaptive Defense 360 is a detection and response service that can accurately classify every process on all your company's endpoints, allowing only legitimate programs to run.
Adaptive Defense 360 relies on a a new security model based on three principles:
![]()
Continuous monitoring of all processes on a company’s computers and servers.
![]()
Automatic classification using Machine Learning on our Big Data platform in the cloud.
![]()
Technical experts who analyze all processes that are not classified automatically, to evaluate the behavior of everything that runs on your systems.
Defending the endpoint against attack is hard. Protection must include a wide range of defenses including traditional antivirus/anti-malware, personal firewall, Web & email filtering and device control. And, any defense must provide additional safeguards against difficult-to-detect zero-day and targeted attacks. Up to now, IT has needed to acquire and maintain a number of different products from different vendors to defend the endpoint.
Adaptive Defense 360 is the first and only offering to combine Endpoint Protection (EPP) and Endpoint Detection & Response (EDR) capabilities into a single solution. Adaptive Defense 360 also automates capabilities reducing the burden on IT. Adaptive Defense 360 starts with Panda's best-of-breed EPP solution which includes Simple and centralized security, Remedial actions, Real-time monitoring and reports, Profile-based protection, Centralized device control, and Web monitoring and Filtering.
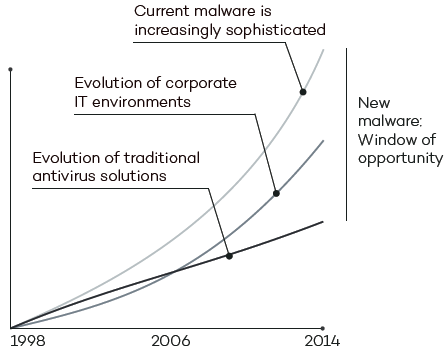
However, that is only the beginning. The malware and IT security environment has undergone major changes in terms of volume and sophistication. With over 200,000 new viruses appearing every day, and the sophistication of techniques for penetrating defenses and hiding malware, corporate networks are more vulnerable than ever to zero-day and targeted attacks.
Traditional Endpoint Protection solutions are efficient at blocking known malware by using detection techniques based on signature files and heuristic algorithms. However, they are no defense against zero-day and targeted attacks that take advantage of the 'window of opportunity for malware,' the time lapse between the appearance of new malware and the release of the antidote by security companies. An increasing gap that is exploited by hackers to get viruses, ransomware, Trojans and other types of malware into corporate networks. Such increasingly common threats can encrypt confidential documents and demand a ransom, or simply collect sensitive data for industrial espionage.
Adaptive Defense is Panda's solution to these types of attacks. Adaptive Defense provides an EDR service that can accurately classify every application running in an organization, only allowing legitimate programs to run. The EDR capabilities of Panda Adaptive Defense 360 relies on a security model based on three principles: continuous monitoring of applications on a company's computers and servers, automatic classification using machine learning on our Big Data platform in the cloud, and finally, our technical experts analyze those applications that haven't been classified automatically to be certain of the behavior of everything that is run on the company's systems.
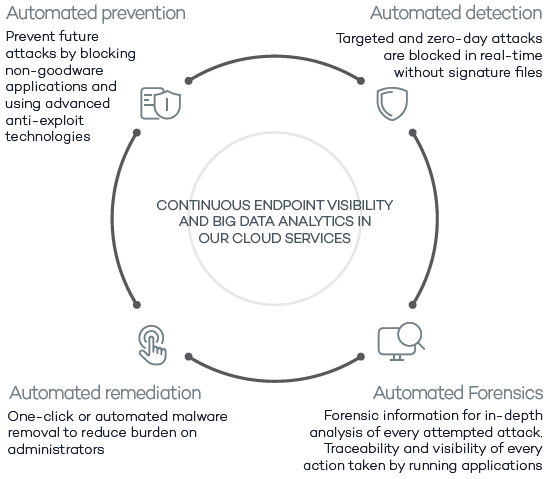
These capabilities are now combined with the best-of-breed EPP solution from Panda, closing the cycle of the adaptive malware protection, which now includes automated prevention, detection, forensics and remediation.
Are you keeping your business data secure?
Confidential data, accounting systems, passwords, customer databases... Bear in mind that eventually someone will try to steal these things. The real question is, will you be able to stop it? Panda Adaptive Defense 360 provides you with a genuine answer to your needs.
With Adaptive Defense 360, we monitor and classify all YOUR software to make sure we discover and stop all malware in YOUR systems.
Adaptive Defense 360 provides automated remediation, real-time monitoring and reports, profile-based protection, centralized control of devices, as well as Web monitoring and filtering.
Features:
Complete, Robust Protection Guaranteed
Panda Adaptive Defense 360 offers two operational modes:
- Standard Mode allows applications classified as goodware to run, as well as those that are yet to be cataloged by the automated systems and Panda Security.
- Extended Mode only allows the execution of goodware.
- Extended blocking is the ideal form of protection for companies with a ‘zero risk’ approach to security.
Forensic Information
- Execution event graphs give a clear view of all events caused by malware.
- Get visual information through heat maps on the destination of malware communications, files created and much more
- Identify and locate the software vulnerabilities on your network.
Full Antivirus Capabilities
Adaptive Defense 360 includes Endpoint Protection capabilities, offering:
- Remediation actions.
- Centralized device control: Prevent malware entry and data loss by blocking certain types of devices.
- Web monitoring and filtering.
- Antivirus and anti-spam for Exchange Server.
- Endpoint firewall, and much more.

100% Automated Service
Forget about having to invest in technical personnel to deal with quarantines or suspicious files or disinfect and restore infected computers. Adaptive Defense 360 automatically classifies all applications using Machine Learning techniques in our Big Data environments, constantly supervised by our PandaLabs technicians.

Continuous Network Status Information
Get alerts as soon as any malware is identified on the network, with detailed information on its location, the devices affected and the type of malware. You will also get email reports about the day-to-day activity of the service.

SIEM Available
Adaptive Defense 360 integrates with SIEM solutions to provide detailed data on the activity of all applications run on your systems. For those without SIEM, Adaptive Defense 360 optionally includes its own security event management and storage system for real-time analysis of all the collected data.
Benefits:

Complete and Robust Protection Guaranteed
Panda Adaptive Defense 360 offers two operational modes:
- Standard mode allows all applications cataloged as goodware to be run, along with the applications that are yet to be cataloged by Panda Security and the automated systems.
- Extended mode only allows the running of goodware. This is the ideal form of protection for companies with a 'zerorisk' approach to security.

Forensic Information
- View execution event graphs to gain a clear understanding of all events caused by malware.
- Get visual information through heat maps on the geographical source of malware connections, files created and much more.
- Locate software with known vulnerabilities installed on your network.

Compatible with Traditional Antivirus Solutions
Adaptive Defense can coexist with traditional antivirus solutions, and take the role of a corporate tool capable of blocking all types of malware, including targeted and zeroday attacks that such traditional solutions are unable to detect.

Protection for Vulnerable Operating Systems and Applications
Systems such as Windows XP, which are no longer supported by the developer and are therefore unpatched and vulnerable, become easy prey for zero-day and new generation attacks.
Moreover, vulnerabilities in applications such as Java, Adobe, Microsoft Office and browsers are exploited by 90% of malware.
The vulnerability protection module in Adaptive Defense 360 uses contextual and behavioral rules to ensure companies can work in a secure environment even if they have systems that are not updated.

Full EPP Capabilities
Adaptive Defense 360 integrates Panda Endpoint Protection Plus, the most sophisticated EPP solution from Panda, thus providing full EPP capabilities, including:
- Remedial actions
- Centralized device control: Prevent malware entry and data loss by blocking device types
- Web monitoring and filtering
- Exchange server antivirus and anti-spam
- Endpoint Firewall, and many others...

Continuous Status Information on all Endpoints in the Network
- Get immediate alerts the moment that malware is identified on the network, with a comprehensive report detailing the location, the computers infected, and the action taken by the malware.
- Receive reports via email on the daily activity of the service.

SIEM Available
Adaptive Defense 360 integrates with SIEM solutions to provide detailed data on the activity of all applications run on your systems.
For clients without SIEM, Adaptive Defense 360 includes its own system for storing and managing security events to analyze all the information collected in real-time.

100% Managed Service
Forget about having to invest in technical personnel to deal with quarantine or suspicious files or disinfect and restore infected computers. Adaptive Defense 360 classifies all applications automatically thanks to machine learning in our big data environments under the continuous supervision of PandaLabs' experts.
Technical Requirements:
| Technical Requirements | |
|---|---|
| Web Console (only monitoring) |
|
| Agent |
|
| Partially Supported (only EPP) |
|
Compare:
| Adaptive Defense 360 | Adaptive Defense | Endpoint Protection | Endpoint Protection Plus | Systems Management | Fusion | Fusion 360 | |
|---|---|---|---|---|---|---|---|
| Protection | |||||||
| Protection against known and zero-day malware | |||||||
| Protection against known and zero-day ransomware | |||||||
| Protection against known and zero-day exploits | |||||||
| Anti-spyware, anti-phishing protection, etc. | |||||||
| Protection for multiple attack vectors (Web, email, network, devices) | |||||||
| Traditional protection with generic and optimized signatures | |||||||
| Protection against Advanced Persistent Threats (APT) | |||||||
| Managed service: Classification of 100% of applications before execution (1*) | |||||||
| Managed service: Threat Hunting (2*) | |||||||
| Queries to Panda’s cloud-based collective intelligence | |||||||
| Behavioral blocking and IoA detection | |||||||
| Personal and managed firewall | |||||||
| IDS / HIDS | |||||||
| Ability to block unknown and unwanted applications | |||||||
| Device control | |||||||
| URL filtering by category (Web browsing monitoring) | |||||||
| Content, Virus and Spam filtering for Exchange Server | |||||||
| Built-in antivirus protection for Exchange Server | |||||||
| Built-in anti-spam protection for Exchange Server | |||||||
| Monitoring | |||||||
| Advanced endpoint security | |||||||
| Cloud-based continuous monitoring of all process activity | |||||||
| Data retention for one year for retrospective attack investigation | |||||||
| Detection | |||||||
| Detection of compromised trusted applications | |||||||
| Managed service: Classification of 100% of applications during and after execution (1*) | |||||||
| Fully configurable and instant security risk alerts | |||||||
| Containment | |||||||
| Real-time computer isolation from the cloud console | |||||||
| Response and remediation | |||||||
| Ability to roll back and remediate the actions committed by attackers | |||||||
| Centralized quarantine | |||||||
| Automatic analysis and disinfection | |||||||
| Investigation | |||||||
| Managed service: Threat Hunting (2*) | |||||||
| Incident graphs and lifecycle information available from the Web console | |||||||
| Ability to export lifecycle information for local analysis | |||||||
| Advanced Visualization Tool (add-on) | |||||||
| Discovery and monitoring of unstructured personal data across endpoints (add-on) | |||||||
| Attack surface reduction | |||||||
| Information about each computer's hardware and software components | |||||||
| Information about the Microsoft updates installed on endpoints | |||||||
| Real-time information about the status of all protections and communications | |||||||
| Unattended, automatic updates | |||||||
| Automatic discovery of unprotected endpoints | |||||||
| Ability to immediately protect unprotected endpoints remotely | |||||||
| Panda native proxy to support endpoints with no Internet connection | |||||||
| Endpoint security management | |||||||
| Centralized cloud-based console | |||||||
| Settings inheritance between groups and endpoints | |||||||
| Ability to configure and apply settings on a group basis | |||||||
| Ability to configure and apply settings on a per-endpoint basis | |||||||
| Real-time deployment of settings from the console to endpoints | |||||||
| Security management based on endpoint views and dynamic filters | |||||||
| Ability to schedule and perform tasks on endpoint views | |||||||
| Ability to assign preconfigured roles to console users | |||||||
| Ability to assign custom permissions to console users | |||||||
| User activity auditing | |||||||
| Installation via MSI packages, download URLs, and emails sent to end users | |||||||
| On-demand and scheduled reports at different levels and with multiple granularity options | |||||||
| Security KPIs and management dashboards | |||||||
| System status reports at different levels and with multiple granularity options | |||||||
| Device inventory and audits | |||||||
| Agent and agentless monitoring of devices | |||||||
| Patch management | |||||||
| Centralized software installation | |||||||
| Non-disruptive remote access | |||||||
| Remote Desktop | |||||||
| Built-in chat | |||||||
| Task automation and scripting | |||||||
| Component store - ComStore | |||||||
| Ticketing/Help Desk | |||||||
| Modules | |||||||
| Panda Data Control integration | |||||||
| Advanced Reporting Tool integration | |||||||
| SIEM integration | |||||||
| Panda Patch Management | |||||||
| Panda Full Encryption inregration | |||||||
| High availability service | |||||||
| Host platform certifications | ISO27001, SAS 70 ISO27001, SAS 70 | ISO27001, FISMA, SAS70, PCI DSS | |||||
| Supported operating systems | |||||||
| Supports Windows | |||||||
| Suppots Exchange | |||||||
| Supports macOS X | |||||||
| Supports Linux | |||||||
| Supports Android | |||||||
| Supports iOS | |||||||
| Support for virtual environments - persistent and non-persistent (VDI)** | |||||||
* Panda Fusion is a bundle of Panda Endpoint Protection Plus and Panda Systems Management. Panda Fusion 360 is the combination of Panda Systems Management and Panda Adaptive Defense 360 that are sold separately
** Compatible systems with the following types of virtual machines: VMWare Desktop, VMware Server, VMware ESX, VMware ESXi, Citrix XenDesktop, XenApp, XenServer, MS Virtual Desktop y MS Virtual Servers. Panda Adaptive Defense 360 & Panda Fusion 360 solutions are compatible with Citrix Virtual Apps, Citrix Desktops 1906 & Citrix Workspace App for Windows, Panda Securtity has been verified as Citrix Ready partner.
1* 100% Classification Service.
2* Threat Hunting and Investigation Service
Documentation:
Download the Panda Adaptive Defense 360 Datasheet (.PDF)

