
Panda Data Control
Monitor sensitive data across endpoints and servers
Panda Security is now a part of WatchGuard Technologies, please visit our WatchGuard Technologies website to learn more about this product!
Overview:
This module is designed to assist organizations in complying with data protection regulations, as well as discovering and protecting personal and sensitive data both in real time and throughout its lifecycle on endpoints and servers.
Panda Data Control is an unstructured data security module, designed to assist organizations in complying with data protection regulations, as well as discovering and protecting personal and sensitive data both in real time and throughout its lifecycle on endpoints and servers. Panda Data Control discovers, audits and monitors unstructured personal data on endpoints: from data at rest to data in use and data in motion.
6 Challenges for companies to comply with the GDPR
- 1 The GDPR affects any organization that stores and handles the data of citizens of the European Union, even if they do not have physical presence in Europe.
- New requirements that will affect the way data protection figures in your IT processes. Naming a Data Protection Officer.
- Requirement to notify the authorities about any security incident involving personal data within 72 hours after the company becomes aware of the personal data violation.
- The GDPR requires greater transparency. Users will be able to request the erasure of their data (“the right to be forgotten”), and will have the right to data portability, the right to access, and the right to be notified of any data violation, among other rights.
- Managing and disclosing personal data while having to control and inform on where it can be found, how it is collected and stored, and who can access it.
- Managing identities and accesses, following applicable identity policies that are transparent and documented, as well as tools that allow for authorization and authentication to guarantee security.
The Solution: Panda Data Control
Panda Data Control is a data security module designed to assist organizations in complying with data protection regulations, as well as discovering and protecting personal and sensitive data both in real time and throughout its lifecycle on endpoints and servers.
Panda Data Control discovers, audits and monitors unstructured personal data on endpoints: from data at rest to data in use and data in motion.
Its powerful custom search engine allows administrators to find any file in the organization with personal data belonging to a specific individual, as well as sensitive information on health, religious beliefs, political views, etc.
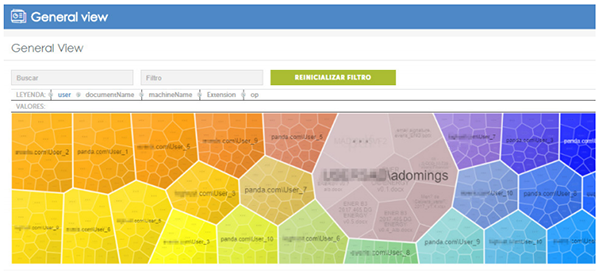
Figure 1 – General view of the files that contain personal information and the users that have accessed to them.
PII Security and Governance
Organizations protected by Panda Adaptive Defense can rest assured that their endpoints and servers won’t be compromised by malicious programs used by external attackers to exfiltrate their data.
Panda Adaptive Defense’s classification service categorizes 100 percent of all applications running on the protected endpoints and servers, returning a verdict on their trustability or malicious nature by using machine learning techniques supervised by Panda Security’s malware specialists. This system ensures that only those applications classified as goodware are allowed to run.
The Panda Data Control module leverages the solution’s EDR (Endpoint Detection and Response) capabilities to continuously monitor the protected endpoints in the organization, discovering and protecting unstructured personal data.
Finally, the Panda Data Control alerts and reports can be customized and adapted to the specific needs of each company.
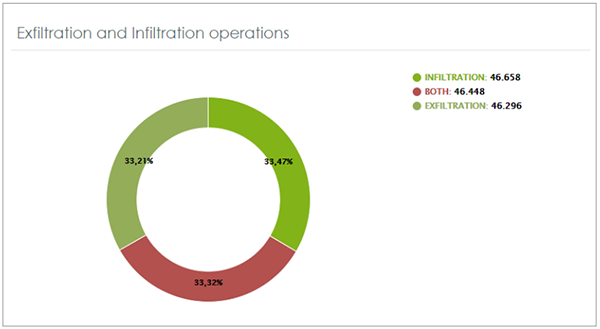
Figure 2 - Operations with files at risk of exfiltration and infiltration: The charts allow you to monitor and assess the risk of the operations performed on PII files by users and machines. This way, Panda Data Control helps organizations adopt measures to prevent and control data exfiltration operations.
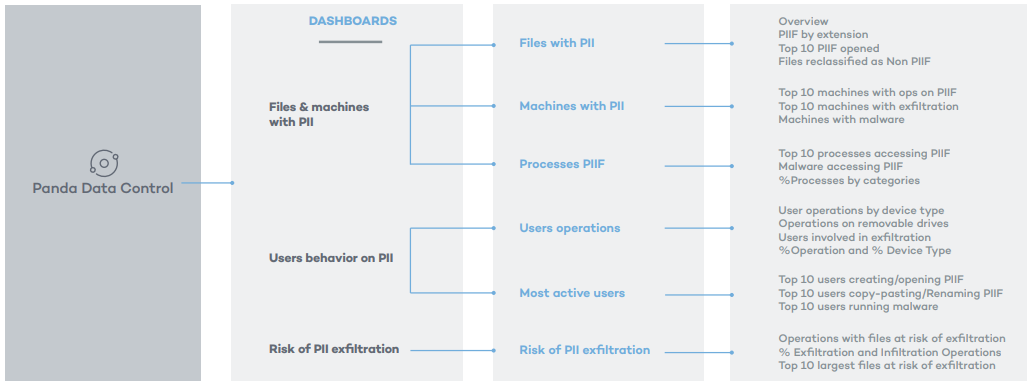
Figure 3 - Panda Data Control – Dashboards, sections, charts and predefined queries.
Features:
Data Discovery:
Automatically classifies and creates an indexed inventory of all files that store unstructured personal data (data at rest), with the number of occurrences of each type of data. These files can be deleted from the inventory. The classification process uses a combination of rules, regular expressions, and machine learning techniques, among others, optimizing classification results while reducing false positives and resource consumption on devices.
Data Search:
Run free custom searches to find files with all sorts of personal data. Panda Data Control will generate a list of all files containing that information, with the option to export it for easier management.
Data Monitoring:
Monitor the various types of operations performed on unstructured files (data in use), while keeping the personal data file inventory fully up to date. Any attempt to copy or move any of these files out of the network via email, Web browsers, FTP or removable storage (data in motion) is recorded by the module.
Data Visualization:
The results of the data monitoring and discovery tasks are continuously synced on the Adaptive Defense platform and in its module Advanced Visualization Tool. This module provides tools for investigating all events affecting data at rest, in use and in motion, both in real time and retrospectively throughout its lifecycle on devices. Panda Data Control’s dashboards and predefined reports and alerts help to cover use cases and ensure security governance of the unstructured personal data.
Benefits:
Discover and Audit
Automatically identify files with personal data (PII) as well as the users, employees, collaborators, endpoints and servers in your organization that are accessing personally identifiable information.
Monitor and Detect
Implement proactive measures to prevent access to PII with the help of reports and real-time alerts on the unauthorized and suspicious use, transmission and exfiltration of personal data files.
Run Custom Searches
Run custom searches of the personal data your organization wants to manage. Its powerful search engine enables administrators to find personal data files, even duplicated ones, accurately based on their own filter criteria.
Simplify Management
The Panda Data Control module is native in Panda Adaptive Defense and Panda Adaptive Defense 360. It doesn’t require organizations to deploy anything other than the standard protection, and can be easily activated. Once activated, the module is enabled and managed from the cloud platform.
Demonstrate Compliance
Demonstrate compliance with relevant regulations to senior management, the DPO, all other employees in your organization, and the Supervisory Authorities. Show the strict security measures in place to protect PII at rest, in use and in transit between endpoints and servers.
Technical Requirements:
Find below the installation requirements for Panda Data Control.
Supported platforms
Panda Data Control supports Microsoft Windows platforms from version XP SP3 and later. Operating systems such as Linux or macOS are not supported.
Recognized data types
Panda Data Control supports the following data types or entities:
- Bank account numbers.
- Credit card numbers.
- Personal and fiscal ID numbers.
- IP addresses.
- Email addresses.
- Phone numbers.
- Driving license numbers.
- Passport numbers.
- Social security numbers.
- First names and last names.
- Postal addresses and ZIP/postal codes.
Supported countries
The format of recognized data varies from country to country. Panda Data Control recognizes data from the countries listed below:
- Germany
- Spain
- France
- Sweden
- UK
- Italy
- Portugal
- Netherlands
- Switzerland
- Finland
- Denmark
- Norway
- Austria
- Belgium
- Hungary
- Ireland
How Panda Data Control Assists With GDPR Compliance:
| GDPR Article | Panda Data Control feature |
|---|---|
| Art. 17: Right to erasure ('right to be forgotten') The data subject shall have the right to obtain from the controller the erasure of personal data concerning him or her without undue delay and the controller shall have the obligation to erase personal data without undue delay ... |
Panda Data Control allows organizations to configure custom searches to find all files on the network that contain personal data of any individual who wants to exercise their right to erasure. Once found, Panda Data Control lets you delete those files from the generated inventory. |
| Art. 32: Security of processing. The controller and the processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk, including a process for regularly testing, assessing and evaluating the effectiveness of technical and organizational measures for ensuring the security of the processing. |
Panda Data Control provides tools for organizations to assess, both in real time and retrospectively, whether the personal data files stored on their network are accessed only by authorized personnel and whether the security policies in place are adequate or not. Available reports include:
|
| Art. 33: Notification of a personal data breach to the supervisory authority. In the case of a personal data breach, the controller shall without undue delay and, where feasible, not later than 72 hours after having become aware of it, notify the personal data breach to the supervisory authority competent. This notification shall describe the nature of the personal data breach including where possible, the categories and approximate number of data subjects concerned and the categories and approximate number of personal data records concerned. |
Panda Data Control offers, in addition to the detailed graphs for compliance with article 32, includes a series of reports specially focused on PII exfiltration:
|
| Art. 35: Data protection impact assessment. Where a type of processing in particular is likely to result in a high risk to the rights and freedoms of natural persons, the controller shall, prior to the processing, carry out an assessment of the impact of the envisaged processing operations on the protection of personal data. |
The Panda Data Control module aims at identifying those files that store personal information, as well as monitoring the actions taken on them and the users involved. This data enables organizations to discover the volume, type and use of the personal information residing on their network, so that they can assess the impact and risk of processing such information. The aforementioned dashboards and reports apply to this article as well. |
| Art. 39: Tasks of the data protection officer (DPO). The data protection officer shall have at least the following tasks:
|
All of the aforementioned dashboards and reports, especially those referring to article 35, are essential tools to help the DPO fulfil their duties. |
Panda Data Control Dashboards:
Art. 32: Security of processing
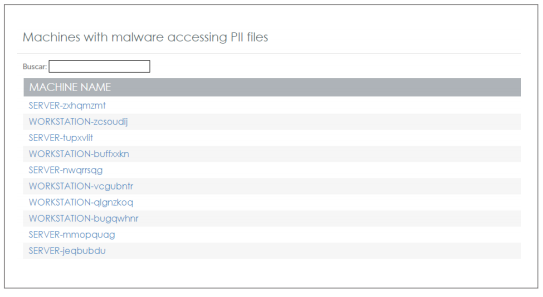
Files and machines with PII Panda Data Control Dashboard - Machines with malware accessing PII files:
This dashboard shows the top 10 computers where malicious processes have been detected accessing personal data. This information allows security administrators to detect recurrent malware infections and persistent threats on certain computers, as well as to assess the impact of these threats on the personal data held by the organization as required by the GDPR.
Art. 33: Notification of a personal data breach to the supervisory authority
User operations on PII files Panda Data Control Dashboard – Distribution of types of operation in PII Files:
This dashboard displays the types of operations performed on the personal and sensitive data files handled by your organization. A significant increase or decrease in the number of any of these operations might indicate a data security incident or event.
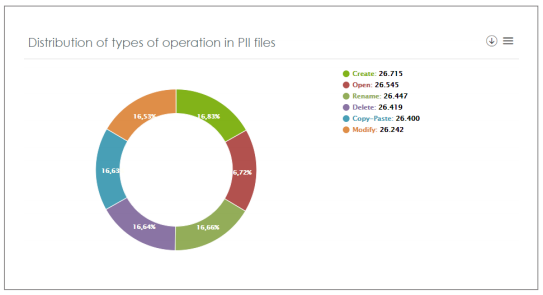
Art. 35: Data protection impact assessment
User operations on PII files dashboard – Top 10 users involved in copy-paste operations:
This graph lists the top users who performed copy-paste operations on files with personally identifiable information (PII). Panda Data Control monitors other types of operations as well: accessing, creating, opening, renaming, deleting, etc.
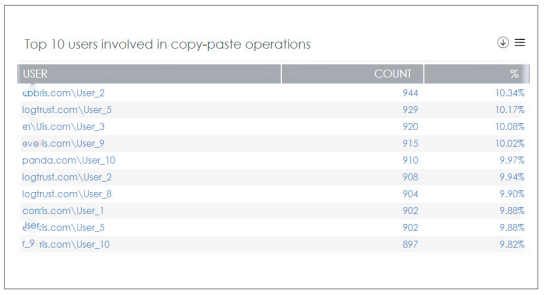
Art. 39: Tasks of the data protection officer (DPO)
Risk of PII exfiltration dashboard - Number of operations with files at risk of exfiltration:
This graph helps organizations monitor personal data flows by displaying the number of exfiltration operations performed on sensitive data files across the network.
This information enables the DPO to determine the usual number of exfiltration operations, and detect deviations caused by security incidents.
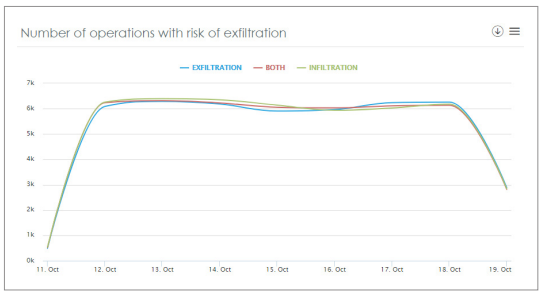
Aether Platform:
 Cloud Based Management Platform
Cloud Based Management Platform
Aether’s cloud-based platform and management console, common for all of Panda’s endpoint solutions, provide optimized advanced and adaptive security management inside and outside the corporate network. Minimize complexity and maximize flexibility, granularity and scalability.
Achieve more in less time. Easy implementation
- Deploy, install and configure the solution in minutes. Immediate value from day one.
- A single lightweight agent for all products and platforms (Windows, Mac, Linux and Android).
- Automatic discovery of unprotected endpoints. Remote installation.
- Proprietary proxy and repository/cache technologies. Optimized communication even with endpoints without an Internet connection.
Simplified operations. Adapts to your organization
- Intuitive Web console. Flexible, modular management that reduces the total cost of ownership.
- Configures users with total or limited visibility and permissions. Action audit.
- Group and endpoint-based security policies. Predefined and custom roles.
- Hardware and software inventories and change log.
Easy scaling of security and management capabilities over time
- No need for new infrastructure to deploy the modules. No deployment costs.
- Real-time communication with endpoints from a single Web console.
- Dashboards and indicators per module.
Compatible solutions within the Aether Platform:
- Panda Adaptive Defense
- Panda Adaptive Defense 360
Documentation:
Download the Panda Data Control Datasheet (.PDF)

