
Panda Fusion 360
Advanced Security, Management and Support from the Cloud
Panda Security is now a part of WatchGuard Technologies, please visit our WatchGuard Technologies website to learn more about this product!
Overview:
Panda Fusion 360 is a holistic solution that provides automated advanced security, centralized IT management, and remote support for all workstations, laptops and servers on the corporate network, including mobile devices and tablets. As it is a cloud solution, it is deployed rapidly without the need for maintenance or costly investments in IT infrastructure.
Panda Fusion 360 combines the best of two worlds. The advanced adaptive security provided by Panda Adaptive Defense 360 against all types of cyberthreats, and the integrated management, monitoring and remote support capabilities delivered by Panda Systems Management.
- Automated prevention, detection, containment and response against any present or future advanced threats, zero-day malware, ransomware, phishing, memory exploits and malwareless attacks.
- Cost savings thanks to centralized control and automation of infrastructure management tasks.
- The best support experience with proactive troubleshooting and remote, unobtrusive access to devices inside and outside the corporate network

Panda Systems Management
Mobility, processing and storage have revolutionized corporate environments, and organizations need tools that can help them improve efficiency and productivity. Panda Systems Management is a solution designed to manage, monitor and support all your organization’s devices, whether they are in the office or on the road.
Benefits
Improves IT management efficiency
- Alerts and monitoring of corporate IT assets.
- Granular visibility into all devices on your network.
- Task automation and streamlined infrastructure management.
- On-demand detailed reports with measurable results for decision makers and external authorities.
- Incident management tool: greater collaboration and improved incident response times.
Increases productivity and reduces IT costs
- Centralized management and support for all computers and devices, delivered from the cloud.
- Network status monitoring helps create and apply software installation policies.
- Unobtrusive support and remote access tools promote user mobility.
- Continuous, real-time visibility into corporate assets (hardware and software inventory) simplifies audits and helps create business budgets.

Panda Adaptive Defense 360
Panda Adaptive Defense 360 is a ground-breaking cybersecurity solution for workstations, laptops and servers, delivered from the cloud. It automates prevention, detection, containment and response against any present or future advanced threats, zero-day malware, ransomware, phishing, memory exploits and malwareless attacks, inside and outside the corporate network. It combines the widest range of endpoint protection technologies (EPP) with automated EDR capabilities, thanks to two services managed by Panda Security experts:
- 100% Attestation Service
Benefits
Simplifies and minimizes the cost of advanced adaptive security
- Its managed services reduce the cost of expert personnel. There are no false alarms to manage, and no responsibility is delegated to administrators.
- Managed services self-learn from threats. No time is wasted with manual settings.
- Maximum prevention on endpoints. Operating costs are reduced practically to zero.
- There is no management infrastructure to install, configure or support.
- Endpoint performance is not impacted as the solution is based on a lightweight agent and cloud architecture.
Automates and reduces response and investigation times
- Automatic and transparent remediation.
- Rapid endpoint activity recovery and immediate return to normal operation.
- Actionable insights into attackers and their activity, speeding up forensic investigation.
- Helps reduce the attack surface. Improves security posture and maturity.
Features:

Traditional Preventive Technologies
- Personal or managed firewall. IDS
- Device control
- Permanent, on-demand antimalware across multiple vectors
- Managed blacklisting/whitelisting. Collective Intelligence
- Pre-execution heuristics
- Web filtering
- Anti-spam and anti-phishing
- Anti-tampering
- Email content filtering
- Remediation and rollback

Prevention, Detection and Response Technologies
- EDR: Continuous endpoint monitoring
- Unknown process execution prevention
- 100% Attestation Service: cloud-based, machine learning behavior analysis service that classifies all processes (APTs, ransomware, rootkits, etc.)
- Cloud-based sandboxing in real environments
- Behavior analysis and IoA detection
- Automatic detection and response to memory exploits

Cloud-based Centralized Management
- Detection of unpatched devices. Automatic patching and patch management.
- Remote, centralized software deployment. Monitoring of CPU, memory and disk space usage, services, software, etc.
- Mobile Device Management (MDM): monitoring of the status of all mobile devices across the organization.
- License management and control. Dashboard alerts.

Real-Time Monitoring and Inventories
- Real-time visibility and control of all devices on the network, including smartphones and tablets.
- Monitoring and control of CPU, memory and disk space usage, services, software, backup execution, etc.
- Performance charts and on-demand detailed status reports with measurable results.
- Software and hardware change logs.

Remote, Automated Support
- Remote connection to agent-based and agentless devices (Telnet/SSH, HTTP, etc.).
- Unobtrusive support: remote event logging, command prompt, task manager, file transfer, registry editor.
- Ticketing system. Troubleshooting and internal communication. Free access to the ComStore.
- Quick jobs, ability to download and customize scripts for automated troubleshooting.
Benefits:

Ticket System For IT
Fusion incorporates a ticket system to organize and classify user incidents and shared troubleshooting procedures.

Remote Control and Messaging
Fusion allows you to remotely access the desktop of all users on the corporate network (shared access or total control), or communicate with them through a messaging system.

Profile-Based Configuration
Assign different protection polices to users through configuration profiles.
Apply different levels of protection according to the profile of the user who connects to your corporate network.

Device Control
Prevent malware entry and data leaks by blocking device categories: USB memory sticks and modems, webcams, DVD/CD drives, etc.
In addition, you can establish exceptions with device whitelists, or simply block certain dangerous actions (access, read, write) on protected devices.

Flexible and Rapid Installation
Deploying Fusion across complex networks has never been easier.
Install the solution on your devices through an email with a download URL, or transparently by selecting each device in the built-in deployment tool (compatible with Active Directory, Tivoli, SMS, etc.).

Malware Freezer
Avoid false positives with Malware Freezer. Freeze the malware detected for seven days and, if it is a false alarm, automatically restore the file on the user's system.
Cloud Based Management Platform:
Aether’s cloud-based platform and management console, common for all of Panda’s endpoint solutions, provide optimized advanced and adaptive security management inside and outside the corporate network. Minimize complexity and maximize flexibility, granularity and scalability.
Achieve more in less time. Easy implementation
- Deploy, install and configure the solution in minutes. Immediate value from day one.
- A single lightweight agent for all products and platforms (Windows, Mac, Linux and Android).
- Automatic discovery of unprotected endpoints. Remote installation.
- Proprietary proxy and repository/cache technologies. Optimized communication even with endpoints without an Internet connection.
Simplified operations. Adapts to your organization
- Intuitive Web console. Flexible, modular management that reduces the total cost of ownership.
- Configures users with total or limited visibility and permissions. Action audit.
- Group and endpoint-based security policies. Predefined and custom roles.
- Hardware and software inventories and change log.
Easy scaling of security and management capabilities over time
- No need for new infrastructure to deploy the modules. No deployment costs.
- Real-time communication with endpoints from a single Web console.
- Dashboards and indicators per module.
System Requirements:
Panda Fusion 360 is a bundle of the following products: Panda Adaptive Defense 360 and Panda Systems Management whereas Panda Fusion is a bundle of Panda Endpoint Protection Plus and Panda Systems Management.
| System Requirements | |
|---|---|
| Operating systems (Workstations) |
|
| Operating systems (Servers) |
|
| Prerequisite in PCSM |
|
| For macOS workstations / file servers* |
|
| For Linux workstations / file servers** |
|
| For smartphones and tablets |
|
| For Exchange Server |
|
| Supports the following virtualization environments |
|
| Compatible browsers |
|
* The PCSM support is provided only on Sierra, High Sierra and Mojave versions.
** Panda Adaptive Defense 360/Panda Endpoint Protection Plus on Aether Platform only works in Ubuntu and Fedora. The PCSM agent may work with any Debian-based distribution but support is only provided for the ones listed.
*** For new installations of the PCSM Linux agent, you must pre-install the Mono runtime.
Compare:
| Adaptive Defense 360 | Adaptive Defense | Endpoint Protection | Endpoint Protection Plus | Systems Management | Fusion | Fusion 360 | |
|---|---|---|---|---|---|---|---|
| Protection | |||||||
| Protection against known and zero-day malware | |||||||
| Protection against known and zero-day ransomware | |||||||
| Protection against known and zero-day exploits | |||||||
| Anti-spyware, anti-phishing protection, etc. | |||||||
| Protection for multiple attack vectors (Web, email, network, devices) | |||||||
| Traditional protection with generic and optimized signatures | |||||||
| Protection against Advanced Persistent Threats (APT) | |||||||
| Managed service: Classification of 100% of applications before execution (1*) | |||||||
| Managed service: Threat Hunting (2*) | |||||||
| Queries to Panda’s cloud-based collective intelligence | |||||||
| Behavioral blocking and IoA detection | |||||||
| Personal and managed firewall | |||||||
| IDS / HIDS | |||||||
| Ability to block unknown and unwanted applications | |||||||
| Device control | |||||||
| URL filtering by category (Web browsing monitoring) | |||||||
| Content, Virus and Spam filtering for Exchange Server | |||||||
| Built-in antivirus protection for Exchange Server | |||||||
| Built-in anti-spam protection for Exchange Server | |||||||
| Monitoring | |||||||
| Advanced endpoint security | |||||||
| Cloud-based continuous monitoring of all process activity | |||||||
| Data retention for one year for retrospective attack investigation | |||||||
| Detection | |||||||
| Detection of compromised trusted applications | |||||||
| Managed service: Classification of 100% of applications during and after execution (1*) | |||||||
| Fully configurable and instant security risk alerts | |||||||
| Containment | |||||||
| Real-time computer isolation from the cloud console | |||||||
| Response and remediation | |||||||
| Ability to roll back and remediate the actions committed by attackers | |||||||
| Centralized quarantine | |||||||
| Automatic analysis and disinfection | |||||||
| Investigation | |||||||
| Managed service: Threat Hunting (2*) | |||||||
| Incident graphs and lifecycle information available from the Web console | |||||||
| Ability to export lifecycle information for local analysis | |||||||
| Advanced Visualization Tool (add-on) | |||||||
| Discovery and monitoring of unstructured personal data across endpoints (add-on) | |||||||
| Attack surface reduction | |||||||
| Information about each computer's hardware and software components | |||||||
| Information about the Microsoft updates installed on endpoints | |||||||
| Real-time information about the status of all protections and communications | |||||||
| Unattended, automatic updates | |||||||
| Automatic discovery of unprotected endpoints | |||||||
| Ability to immediately protect unprotected endpoints remotely | |||||||
| Panda native proxy to support endpoints with no Internet connection | |||||||
| Endpoint security management | |||||||
| Centralized cloud-based console | |||||||
| Settings inheritance between groups and endpoints | |||||||
| Ability to configure and apply settings on a group basis | |||||||
| Ability to configure and apply settings on a per-endpoint basis | |||||||
| Real-time deployment of settings from the console to endpoints | |||||||
| Security management based on endpoint views and dynamic filters | |||||||
| Ability to schedule and perform tasks on endpoint views | |||||||
| Ability to assign preconfigured roles to console users | |||||||
| Ability to assign custom permissions to console users | |||||||
| User activity auditing | |||||||
| Installation via MSI packages, download URLs, and emails sent to end users | |||||||
| On-demand and scheduled reports at different levels and with multiple granularity options | |||||||
| Security KPIs and management dashboards | |||||||
| System status reports at different levels and with multiple granularity options | |||||||
| Device inventory and audits | |||||||
| Agent and agentless monitoring of devices | |||||||
| Patch management | |||||||
| Centralized software installation | |||||||
| Non-disruptive remote access | |||||||
| Remote Desktop | |||||||
| Built-in chat | |||||||
| Task automation and scripting | |||||||
| Component store - ComStore | |||||||
| Ticketing/Help Desk | |||||||
| Modules | |||||||
| Panda Data Control integration | |||||||
| Advanced Reporting Tool integration | |||||||
| SIEM integration | |||||||
| Panda Patch Management | |||||||
| Panda Full Encryption inregration | |||||||
| High availability service | |||||||
| Host platform certifications | ISO27001, SAS 70 ISO27001, SAS 70 | ISO27001, FISMA, SAS70, PCI DSS | |||||
| Supported operating systems | |||||||
| Supports Windows | |||||||
| Suppots Exchange | |||||||
| Supports macOS X | |||||||
| Supports Linux | |||||||
| Supports Android | |||||||
| Supports iOS | |||||||
| Support for virtual environments - persistent and non-persistent (VDI)** | |||||||
* Panda Fusion is a bundle of Panda Endpoint Protection Plus and Panda Systems Management. Panda Fusion 360 is the combination of Panda Systems Management and Panda Adaptive Defense 360 that are sold separately
** Compatible systems with the following types of virtual machines: VMWare Desktop, VMware Server, VMware ESX, VMware ESXi, Citrix XenDesktop, XenApp, XenServer, MS Virtual Desktop y MS Virtual Servers. Panda Adaptive Defense 360 & Panda Fusion 360 solutions are compatible with Citrix Virtual Apps, Citrix Desktops 1906 & Citrix Workspace App for Windows, Panda Securtity has been verified as Citrix Ready partner.
1* 100% Classification Service.
2* Threat Hunting and Investigation Service
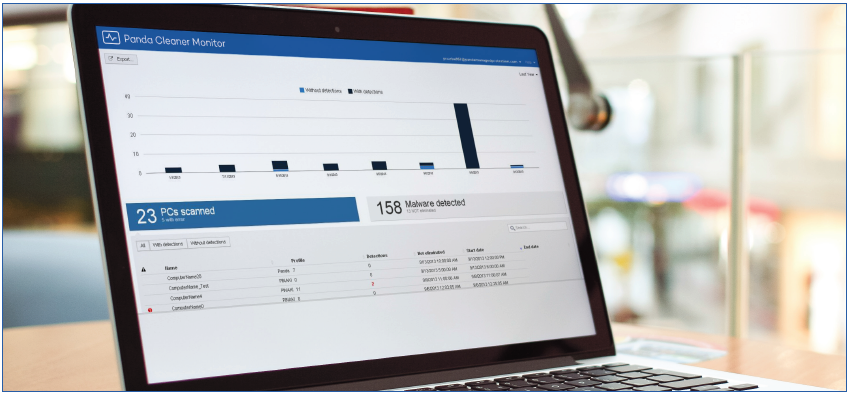
Cleaner Monitor:
Do you think your network could be infected, even though your antivirus tells you otherwise?
This is an advanced disinfection tool that runs a complete scan based on Collective Intelligence or cloud scanning in order to eliminate malware that traditional antivirus products are unable to detect. The benefits of having 25 years' experience detecting and disinfecting malware have enabled us to develop a solution that can monitor all the scans on your network and eliminate any latest generation viruses detected, remotely and from a centralized point.
![]()
Latest Technology
Includes the latest technologies, which are more aggressive than conventional antivirus solutions in detecting and disinfecting latest threats.
![]()
Automatic Reset
Cuts out the manual tasks of restoring infected systems, automatically undoing the changes made by malware to operating systems and restoring system policies.
![]()
Central Monitoring
Stores all scan and disinfection results in a single cloud-hosted repository for all computers on the network. Access it through a simple Web browser and get the information that you need.
Compatible Con:
- Windows 8 (32 and 64-bit)
- Windows 7 (32 and 64-bit)
- Windows Vista (32 and 64-bit)
- Windows XP SP2 or later (32 and 64-bit)
- Windows 2000 Professional
- Windows Server 2003 (32 and 64 bits)
- Windows Server 2008
- Windows Server 2008 R2
- Windows Server 2012 (32 and 64 bits)
Documentation:
Download the Panda Fusion 360 Datasheet (.PDF)

