
Panda SIEM Feeder
Integration with corporate SIEM systems, to add the details and context of everything that runs on your IT network
Panda Security is now a part of WatchGuard Technologies, please visit our WatchGuard Technologies website to learn more about this product!
 Overview:
Overview:
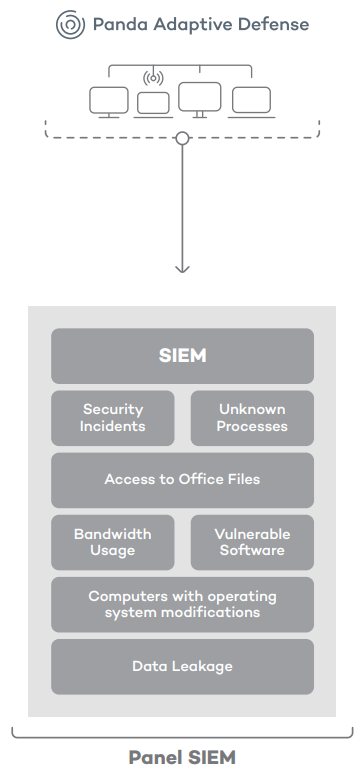
Panda Adaptive Defense seamlessly integrates with existing corporate SIEM solutions without additional deployments on users’ devices. Helping administrators filter the huge volumes of data handled by your SIEM system and focus on what really matters.
A new source of information: User programs
System Information and Event Management (SIEM) solutions have become a necessity to manage the security of both large and mid-sized IT infrastructures. Their capabilities to collect and correlate the status of IT systems allow organizations to turn massive volumes of data into useful information for decision making.
Integrate a new source of critical information into the security intelligence collected and correlated by your SIEM: all processes and programs run on your devices and continuously monitored by Panda Adaptive Defense.
A new security status
IT Departments require high levels of visibility and control to be able to anticipate the security problems caused by next-generation malware.
Panda Adaptive Defense helps administrators filter the huge volumes of data handled by SIEM systems and focus on what really matters:
- What new programs are being run and are yet to be classified as goodware or malware?
- How did those programs reach the network? What suspicious activities are they performing on user devices (registry editing, hooks, driver installation, etc.)?
- What legitimate software with known and exploitable vulnerabilities is being used?
- What processes are accessing user documents and sending information out?
- What is the network usage of each process run on the IT network?
Seamless integration and operation
Panda Adaptive Defense seamlessly integrates with existing corporate SIEM solutions without additional deployments on users’ devices. Monitored events are sent securely using the LEEF/CEF formats compatible with most SIEM systems on the market either directly or indirectly via plugins.
System Requirements:
Panda Importer v1.0.3 is an application, compatible with Windows operating systems, designed to download the logs generated by Panda SIEMFeeder and stored on the Azure platform. Once downloaded, Panda Importer decompresses the logs and stores them automatically in a local or remote folder, as chosen by the customer.
Prerequisites for installation
Read the installation prerequisites of Panda Importer v1.0.3
- Required information:
- Email address used to log in to the Panda Adaptive Defense based on Aether.
- Password associated with the email address used to log in to the Panda Adaptive Defense based on Aether.
- Aether user with the Full Control role.
- Customer code.
- Required operating system and libraries on the computer that will run Panda Importer v1.0.3:
- It has .NET Framework 4.61 installed. If an earlier version is installed, download .NET Framework 4.61.
- Supported operating systems: Windows 10, Windows 7 Service Pack 1, Windows 8, Windows 8.1, Windows Server 2008 R2 SP1, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016 and Windows Server 2019.
- Minimum hardware requirements: processor running at 1 GHz or faster. 512 MB of RAM, 2.5 GB of free hard disk space.
Installing Panda Importer v1.0.3
- Generating the configuration file
- Download the Panda Importer v1.0.3 tool by clicking the Download button file and extract the pandaeventsfeederimporterpro.zip file to a folder of your choice. The file is protected with password panda.
- Make sure the user that runs the program has Local Administrator or Domain Administrator permissions on the computer.
- Run the EventsFeederImporter.Host.exe program from the Command Prompt window or by double-clicking on it.
- The program will ask for the following information:
- Change of settings (Do you want to change the configuration settings?): Answer Yes to generate a new configuration.
- Email address used to log in to the Panda Adaptive Defense.
- Password associated with the email address used to log in to the Panda Adaptive Defense.
- Customer ID specified in the Welcome email. Once entered, Panda Importer will generate an access token it will use internally to sign up to the service and download the generated log files.
- Path to the folder Panda Importer will download the log files to. This folder must have been previously created.
- Panda Importer will use this information to update the configuration.json file located in the same folder as the program, and start downloading the log files.
Running and stopping Panda Importer v1.0.3
- To run Panda Importer v1.0.3, double-click it or run it from the Command Prompt window. The program will ask if you want to change the configuration settings. If you already created a configuration and it is correct, click N.
- To stop Panda Importer v1.0.3, press Control+C in the Command Prompt window.
Changing the Panda Importer settings
Follow these steps to change the Panda Importer settings:
- Stop the process if it is running (Control + C).
- Run Panda Importer again and answer Y to the question Do you want to change the configuration settings?
- Enter the information detailed in section Generating the configuration file.
- Editing the configuration file
The configuration.json file is located in the same folder as Panda Importer, and contains the program's execution parameters.
The first time it is run, the program asks for certain authentication information it later dumps into the configuration file. Once the installation and execution processes are completed for the first time, you'll be able to edit the configuration file in order to adjust some of its settings.
The configuration.json file uses the JSON syntax. Its editable parameters are as follows:- fullPath: Absolute path to the folder that the log files will be downloaded into.
- fileSizeLimitInBytes: Maximum allowed size of the log files.
- directoryMaxSizeInMb: Maximum allowed size of the folder that stores the log files.
- FileSplitFormat: Log file name format, and generation interval:
- "1h" or empty: Format yyyyMMdd-HH. The file name does not specify the minutes of the time. A file is generated every hour. HH indicates the hour of the time when the log file was generated.
- "1m": Format yyyyMMdd-HHmm. A log file is generated every minute. HHmm indicates the hour and minutes of the time when the log file was generated
- "5m": Format yyyyMMdd-HHmm. A log file is generated every 5 minutes. HHmm indicates the hour and minutes of the time when the log file was generated.
- "10m": Format yyyyMMdd-HHmm. A log file is generated every 10 minutes. HHmm indicates the hour and minutes of the time when the log file was generated.
- "15m": Format yyyyMMdd-HHmm. A log file is generated every 15 minutes. HHmm indicates the hour and minutes of the time when the log file was generated.
- "30m": Format yyyyMMdd-HHmm. A log file is generated every 30 minutes. HHmm indicates the hour and minutes of the time when the log file was generated.
- Editing the configuration file
Panda Importer execution log
All operations executed by Panda Importer are logged to text files stored in the Log subfolder inside the program folder.
Documentation:
Download the Panda Siem Feeder on Azure Datasheet (.PDF)

