
Panda Systems Management
The New Way to Manage, Monitor and Support IT Systems
Panda Security is now a part of WatchGuard Technologies, please visit our WatchGuard Technologies website to learn more about this product!
Overview:
Manage Your IT Infrastructure Simply and Proactively with a Rapidly Integrated Solution
Panda Systems Management is the easy and affordable way to manage, monitor and maintain all your organization's devices, whether they are in the office or remote. Thanks to the simplicity offered by the pre-configured settings, the learning curve is practically non-existent, and it ensures that the organization's IT infrastructure operates exactly according to plan.
Why opt for System Management?
- It frees up your IT team to concentrate on value-added projects
- It resolves problems proactively
- It enhances support for new technologies and encourages adoption of BYOD
The new way to monitor and support IT system
Systems Management allows simple and affordable management, monitoring and support of all the devices in your company, whether they are in the office or on the move.
Why you need an IT management solution like systems management
100% cloud-based solution
All operations are performed in the cloud. You do not need any additional infrastructure to centrally manage all of your devices, smartphones and tablets.
The best proactive support for your users
Resolve your users' problems proactively by remotely and non-intrusively accessing their computers and devices, wherever they are.
Secure access to the service
Twofactor authentication to verify identities. Encrypted communication with the server.
Alerts and monitoring
Monitor use of CPU, memory and hard disks, printers low on ink etc., with real-time graphs and alerts.
Rapid tasks and scripts
Create your own scripts or download them from our ComStore. You can also modify them to suit your needs and launch them.
Patch management
Automate the deployment of updates and patches for the software installed.
Software deployment
Centrally deploy software and updates.
Minimize maintenance costs
Systems Management allows you to optimize the functioning of your IT infrastructure thanks to its automated management and centralized control.
Ticket system
Organize, classify and prioritize incident troubleshooting. Share and reuse technical procedures to resolve incidents.
Manage smartphones and tablets (MDM)
Establish password policies, control over use of the device, remote connectivity settings, remote locking and data wiping.
Security certificates
FISMA, SAS70, ISO 27001 and PCI DSS.
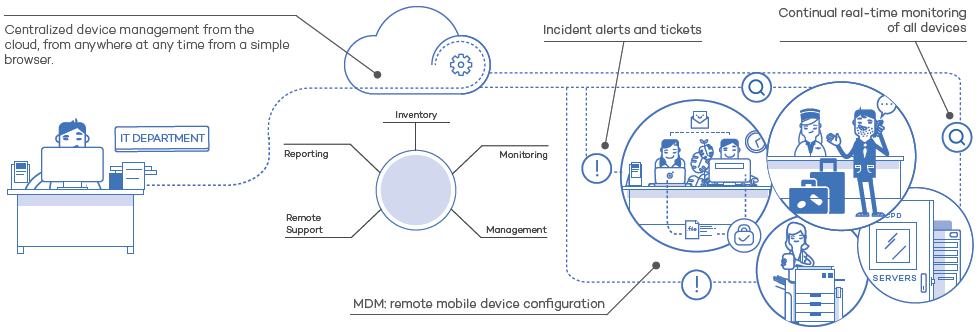
Features:

Take Control of IT: Asset Management
Control your devices:
- 100% granular visibility of the devices you manage
- Stay up-to-date on your IT environment and changes
- Keep a check on the hardware and software installed and in use

Stop Fire-Fighting and Reduce Your IT Costs
Cut out repetitive tasks and phone calls; be proactive:
- The real-time alerts let you identify printers low on toner, servers with little disk space and many other problem indicators
- Automate repetitive tasks
- The events logs display information for each device
- Patch management to keep all devices up-to-date

Keep It Centralized and Simple
Manage your IT resources from a single Web console with all the information and tools you need:
- Cloud-hosted; with no additional infrastructure
- Manage all your devices no matter where they are at any time and from anywhere
- Almost non-existent learning curve

Offer Users the Best Support Experience, No Matter Where They Are
Drastically reduce calls to support:
- Monitor and deliver remote support to all devices, even if they are switched off
- Use diagnostics and non-intrusive problem resolution to increase productivity
Evaluate productivity:
- See who's done what at what time and with what device, etc
- It lets you see reductions in downtime and support time
- Identify problematic hardware/software

Don't Lose Sight of Your Smartphones and Tablets
A single tool lets you monitor and manage all your mobile devices:
- Locate stolen devices and prevent loss of data when devices are lost or stolen with password protection and remote data wiping
- Improve device security by setting standards for the passwords chosen by users.*
- Block non-productive features (installation of games and apps, use of cameras, movies, etc.)*
- Centrally configure VPN and Wi-Fi settings for all devices.*
* Available for iOS platforms
Benefits:

Secure Device Management
Ensure the security of the service through encrypted connections between the devices and the server.
Secure access to the administration console through two-factor authentication in order to check the identity of the administrator.

Remote Control and Messaging
With Systems Management, you can remotely access the desktop of the computers on the corporate network (shared access or total control).
Users can also open tickets to ask for help or communicate directly with the IT department through the messaging and chat system.

Control Your Smartphones and Tablets
Systems Management integrates control and management of mobile devices in a single tool.
Prevent data loss on stolen devices through password-based security and remote wiping.
Find lost or stolen devices and control the apps installed on each device.
Inventory:
Business challenge: You can’t manage it if you don’t know it exists
Do you have 100% permanent visibility of all hardware and software on your IT estate? With dispersed offices around the country, and with an ever increasing number of road warriors and home workers, it’s really difficult to know what you’ve got out there.
However, due to compliancy issues, annual budgeting and “one off” projects, you need to be able to locate that information quickly, without having to send technicians from one office to another, filling excel sheets.
The solution: Know what you have
Systems Management Inventory module will provide you with permanent up-to-date information and complete visibility of all your IT devices.
All inventory data at your finger tips
How many “once off” tasks does your IT dept run per year related to software / hardware? Whether it is for a compliancy audit or budgeting for your HW for the next year these tasks are generally time consuming. With Systems Management you can access all hardware and software centrally for one, some or all devices.
Get an overview of your entire IT estate at a glance
Quickly get a global view of your entire IT estate form one dashboard. See how many devices are online / offline. How many devices are not protected by Antivirus / Firewall?. How many patches your system is missing?
Drill down and get to the point: Filters
Filter all hardware and software data from your entire company in seconds for information from which devices has the older version of a specific application, which machines have less the 4 GB free space on the hard disk and many more
Know how many licenses you are using
Define thresholds for software licenses to ensure you are not exceeding your limit and identify which specific devices have the software in question installed.
How much energy is your IT system consuming?
From the energy usage audit not only can you see what you have got you can also see how much energy it is consuming and how much that energy is costing your company. Drill down and see how much each specific device costs. This can help you to implement and track green initiatives in your company.
Expediting troubleshooting: Change logs
How much time is generally spent on diagnosing end user issues? Over email or by the phone the general question is “What did you do to your PC?” to which the answer is generally “nothing, honest!” The change log will show you all systems, hardware and software changes expediting troubleshooting by identifying incident triggers in a fraction of the time.
So what’s included?
- Hardware and software inventory
Control what software is installed on which devices. Define and control what software can and cannot be used on one, some or all devices. - Hardware/Software/ System change logs
Expedite problem diagnostics by getting all information on your hardware/software and system changes for each device at a glance. - Software licensing control
Keep track of the number of licenses for any software package used across your entire IT estate
Monitoring:
Business challenge: Usually, when you know about it, it’s already too late
If your IT Dept. receives an email or phone call about a server outage or a PC that isn’t working properly, it’s already too late, your company productivity is already affected and the costs are accumulating quickly.
Companies are more IT dependent than ever. From email programs & applications that affect your employees’ productivity to important financial data on your servers that can potentially damage your company’s reputation or affect your bottom line. Waiting for the phone to ring is not enough!.
The solution: Anticipate problems proactively
Systems Management anticipates problems proactively, monitoring device activity through alerts, dashboards, graphs, tickets, etc. This lets you detect incidents and manage time efficiently, automatically allocating them to your IT staff and documenting all actions. This is the only way to improve your response time and prevent major problems that impact negatively your company’s performance and finances.
One step ahead of the problem!
Knowing if something has gone wrong means you can reduce the impact of the problem, knowing if something is going to go wrong means you can avoid it altogether. Establish monitors / alerts to track your IT systems performance and identify issues before they become problems.
Real time monitoring, real time support and tracking
If something has gone wrong on your IT system (server crash) or if something is going to go wrong (possible disk failure), knowing about it in real-time is a must have and not a “nice to have”. With Systems Management, you can set warnings and thresholds for your most important assets and schedule the tasks required to resolve issues proactively.
Monitor and respond automatically
Do not just establish what you should monitor; establish how your system should respond in the case of an issue. So whether it is starting your backup service when it stops or bringing a machine online when it has gone offline you define how your system should respond automatically to a given issue.
Tickets system
Sooner or later incidents build up and technicians have difficulty in prioritizing them and assigning them to department staff.
Moreover, many incidents are quite similar and often require responses already known to the technicians that dealt with them. The tickets system ensures reduced response time and optimizes the operation of the IT department.
Guarantee email continuity
Email is one of the most important communication tools in today’s companies and when that stops the impact can be disastrous. Monitor the most important mail server variables such as queue size, database size etc and preempt email downtime.
Avoid data loss: Ensure back ups are running smoothly
Ensure correct backup execution and avoid data loss by establishing back up monitors. Automatically and in real time monitor that the backup service is installed, running and has been executed in a defined time frame.
The list of options goes on...
The examples mentioned above are just some of the more tangible examples of monitors / alerts that you can create but the possibilities are endless
So what’s included?
- Performance monitoring
Monitor low disk space, CPU usage, memory usage and the status of all your computers, ensuring optimum performance. - Process and service control
Keep on running! Keep your servers running by monitoring those critical services which keep your business working perfectly. - Automatic incident resolution
Define how your system should respond if an alert is triggered; restart services, launch a script, etc. - Tickets system
Creation of tickets to manage incidents and ensure they are allocated efficiently across your technical team, encouraging exchange of information and re-use of technical procedures.
Management:
Business challenge: Daily maintenance tasks take too much time
The challenges associated with managing an ever more complex and dispersed IT infrastructure are becoming harder and harder.
Today, IT administrators have to manage a wide variety of devices. They have to deal with the need to constantly change and upgrade software for maximum productivity, security and stability. All of this with an ever-growing dispersed workforce who can now work from the office, from home, from the airport, etc.
The solution: Automate maintenance tasks centrally
As Gartner says, “Effective management can cut total cost of ownership for desktop PCs by 42 percent.” With Systems Management you can centrally automate critical tasks, saving time and money. Improve your security by keeping software and patches up-to date.
Increased stability and security = decreased downtime
Ensuring all devices you manage are up to date and secure directly and dramatically reduces the number of device incidents while also reducing the impact of downtime.
Patch management polices
Making sure your machines are patched is a must have but also a difficult task to manage in companies that have dispersed offices and mobile staff. Create Microsoft patch policies for one, some or all your devices regardless of if they are on the LAN or not. Patches can also be rollout on demand or scheduled.
Centrally distribute and update company software
Whether it is your internal CRM application, a program for your finance department or MS Office for administration; it needs to be deployed and updated. Centrally deploy and update all your companies’ software and track all deploys to ensure they have run correctly, regardless if the device is on the LAN or on the road.
3rd party software updates/patches
Keeping your operating systems up to date is critical but so too is managing the update of 3rd party software such as browsers, Adobe, Flash, Java etc. From our Comstore you can download from our ever extending range of 3rd party software and distribute directly to a device (s) or schedule the deploy / update.
Scripting: Pre-prepared or create your own
Centralizing scripts on one platform means that technicians can collaborate and use the same tools. You can directly create scripts in multiple languages and make them available to all technicians.
Can’t script? No problem, you can also download and edit scripts ready from Systems Management for common tasks such as disk defragmentation, analyze the memory, or delete print queues to name a few ...
Power management/policies
Define how your devices should power off and use energy more efficiently. Schedule shutdown, sleep and hibernation times for one, some or all devices. In addition, define times for turning off hard disks, displays etc. Do this in seconds and measure the impact on you energy usage via the Energy Audit report.
Run and monitor regular health checks
Reduce the overall number of incidents by ensuring your devices are running smoothly. Schedule regular health checks, such as memory checks, disk checks, disk fragmentation and monitor the results to guarantee that everything runs smoothly.
So what’s included?
- Centralized patch management
Ensure your devices have the latest updates and patches keeping them in good health. - Script execution
Build your own scripts or download prepared, prepackaged scripts from our component store, and launch them with a single click of a button, schedule or as an automatic response to an alert. - Automate software deployment
Centrally deploy and upgrade software, ensuring your environment has the most secure and stable version available. Ensure the highest levels of security, stability & productivity for end users. - Enforce power management policies
Go Green and optimize your IT carbon footprint.
Smartphone and Tablet Management
The challenge: The mobility of today’s workforce and the wide variety of mobile device platforms available make control and management significantly more difficult.
The use of mobile devices in the business world is clearly on the rise. Not only that, according to The Times, with the appearance of smartphones and tablets the average number of mobile devices business executives use rose to 3.4 in 2012.
As if this was not enough, the existence of multiple mobile platforms competing for the same niche market has made network management even harder and fostered the appearance of fragmented management solutions with very different functionalities.
The solution: A single, cloud-based mobile device management solution for your entire organization.
Systems Management lets you manage your Android and iOS devices, both in the office and on the road, from a single Web-based console accessible anywhere, anytime. Log software and hardware changes on mobile devices and generate reports on the status of your mobile fleet.
What does it offer?
- Single Web-based console
For centrally managing all your Windows and Mac OS X laptops (netbooks, ultrabooks, etc), tablets, Android and iOS smartphones, both in the office and on the road, anywhere, anytime. - Monitoring of the status of your mobile devices (online/ offline)
Hardware and software installed, changelogs, operating system and version, operator, total capacity and free space in internal drives, etc. - Consolidated reports
Showing the status of all devices on your network, including smartphones, tablets and laptops.
Remote Support:
Business challenge: Solving IT incidents is usually too intrusive, affecting end-user productivity
Quite often, when problems arise, troubleshooting is intrusive for end users. Support technicians must travel or connect to devices, taking control of them and directly and negatively affecting end-user productivity.
The solution: Connect remotely, wherever you are, and resolve issues non-intrusively
With Systems Management, technicians can remotely connect to the devices, even if they are switched off, run diagnostics and resolve issues transparently for end users, wherever they are.
The console includes built-in remote access tools that provide access to devices in the background. In addition, it allows you to run commands, view and manage event logs, registry entries, services and transfer files without disturbing users.
Anywhere to anywhere connectivity
All you need is an Internet connection and to install the agent in order to access end-user devices remotely, regardless of whether the device is switched off and no matter the location of the device or the administrator.
Hassle free centralized direct access
How long does it usually take you to connect to a remote machine from the time you know a problem exists? What happens if the device is switched off and the office deserted? With Systems Management, simply click the Wake on Lan option and you can connect directly to the device remotely, with no need for additional software or downloads.
Extensive tool set for problem diagnostics
Real time information on:
- Task manager (processes, performance stats etc.)
- Services
- Registry
- Event logs
- Command shell
- Screenshots
- File transfer
No concurrent connection limitation
You or other technicians can establish as many remote connections as you need without the fear of disconnecting other sessions due to concurrent session limitations.
Non intrusive or take over
You can take over the end users session, like the majority of remote control software, or you can connect non-intrusively in the background. While connected in the background you can identify the problem and resolve it without the end user ever knowing you were connected and what’s more important without ever affecting his / her productivity.
Direct access to remediation tools
You can take remediation action by using the command shell, killing processes, restarting services etc but also by directly accessing all your applications; software, scripts. You can also shutdown or restart the device, normally or in safe mode all remotely.
Chat and take notes
You can chat to the end user using the realtime chat option and also take notes on the connection which are saved to the devices information for future reference.
So what’s included?
- Remote access
Start your devices remotely and access them wherever they are. - Remote tools
Task manager, file transfer, registry editor, event log viewer... Builtin remote tools let you fix multiple devices without interrupting users. - Remote control
Desktop access shared with the user or full control. You can also chat with the end user. - Single management console for support
Assign and track incidents supporting documentation with the ticket system.
Reporting:
Business challenge: It’s really difficult to show the value of your work
It is useless to provide users with the best service if they don’t notice it and even complain about IT technicians. How many times have you been told that it takes too long for you to resolve incidents? How many users would feel more satisfied if they knew what you actually do for them? Also, how can you show the value of your work to your IT Director?
The solution: Use detailed reports to show the true value of your work
With the detailed and measurable reports of Systems Management, you can justify the time spent and show all the actions you have taken remotely, preventing and managing problems.
Everything is tracked
While you are deploying software, updating patches, executing scripts and connecting remotely to devices, too mention but a few, all that information is tracked and stored so you can leverage it later in your reports.
Demonstrating value
Remotely managing, monitoring and supporting your IT estate can be difficult to demonstrate as it would appear that everything runs smoothly by itself. Using a wide range of reports you can get unique insights into your IT system and quickly show why your IT system is running smoothly.
On demand or scheduled
Schedule your most commonly needed reports such as weekly activity reports or health checks and configure the report to be sent to key stakeholders via email periodically. You can also respond to once off requests for IT information by creating on demand reports in closed or open formats which can complement other documents.
Activity reports
Keep track of all your support activities. Identify quickly how many jobs have been done (software installations, health checks etc.), remote support sessions and which technicians executed them and when.
User software installations
Lets you know exactly what software your end users have installed, updated or deleted. You will also know the version in question and the date and time of the action.
Storage capacity
Quickly identify the devices that are running out of space with this graphical report on storage usage on the various devices and each drive.
Alert reports
Identify which alerts (e.g. a certain service stopped) have been triggered and on which devices, if there was a response to the alert and the average time of the response. This report also gives you insight into the devices that are most problematic.
So what’s included?
- Detailed activity reports
See your network activity in detail: remote connections, software installation, patches installed, bandwidth consumption, etc. - Automatic reports
Email on-demand or scheduled reports. - Device profile reports
Make a list of all devices within your network: name, IP address, hardware and software name, etc. Generate network status summaries. - Complete license reports
Find out which operating systems and software users have on their PCs (quantity & type).
Technical Requirements:
| Technical Requirements | |
|---|---|
| For Windows |
|
| For Apple Macintosh |
|
| For Linux |
|
| For Smartphones and Tablets |
|
| Compatible Browsers |
|
Compare:
| Adaptive Defense 360 | Adaptive Defense | Endpoint Protection | Endpoint Protection Plus | Systems Management | Fusion | Fusion 360 | |
|---|---|---|---|---|---|---|---|
| Protection | |||||||
| Protection against known and zero-day malware | |||||||
| Protection against known and zero-day ransomware | |||||||
| Protection against known and zero-day exploits | |||||||
| Anti-spyware, anti-phishing protection, etc. | |||||||
| Protection for multiple attack vectors (Web, email, network, devices) | |||||||
| Traditional protection with generic and optimized signatures | |||||||
| Protection against Advanced Persistent Threats (APT) | |||||||
| Managed service: Classification of 100% of applications before execution (1*) | |||||||
| Managed service: Threat Hunting (2*) | |||||||
| Queries to Panda’s cloud-based collective intelligence | |||||||
| Behavioral blocking and IoA detection | |||||||
| Personal and managed firewall | |||||||
| IDS / HIDS | |||||||
| Ability to block unknown and unwanted applications | |||||||
| Device control | |||||||
| URL filtering by category (Web browsing monitoring) | |||||||
| Content, Virus and Spam filtering for Exchange Server | |||||||
| Built-in antivirus protection for Exchange Server | |||||||
| Built-in anti-spam protection for Exchange Server | |||||||
| Monitoring | |||||||
| Advanced endpoint security | |||||||
| Cloud-based continuous monitoring of all process activity | |||||||
| Data retention for one year for retrospective attack investigation | |||||||
| Detection | |||||||
| Detection of compromised trusted applications | |||||||
| Managed service: Classification of 100% of applications during and after execution (1*) | |||||||
| Fully configurable and instant security risk alerts | |||||||
| Containment | |||||||
| Real-time computer isolation from the cloud console | |||||||
| Response and remediation | |||||||
| Ability to roll back and remediate the actions committed by attackers | |||||||
| Centralized quarantine | |||||||
| Automatic analysis and disinfection | |||||||
| Investigation | |||||||
| Managed service: Threat Hunting (2*) | |||||||
| Incident graphs and lifecycle information available from the Web console | |||||||
| Ability to export lifecycle information for local analysis | |||||||
| Advanced Visualization Tool (add-on) | |||||||
| Discovery and monitoring of unstructured personal data across endpoints (add-on) | |||||||
| Attack surface reduction | |||||||
| Information about each computer's hardware and software components | |||||||
| Information about the Microsoft updates installed on endpoints | |||||||
| Real-time information about the status of all protections and communications | |||||||
| Unattended, automatic updates | |||||||
| Automatic discovery of unprotected endpoints | |||||||
| Ability to immediately protect unprotected endpoints remotely | |||||||
| Panda native proxy to support endpoints with no Internet connection | |||||||
| Endpoint security management | |||||||
| Centralized cloud-based console | |||||||
| Settings inheritance between groups and endpoints | |||||||
| Ability to configure and apply settings on a group basis | |||||||
| Ability to configure and apply settings on a per-endpoint basis | |||||||
| Real-time deployment of settings from the console to endpoints | |||||||
| Security management based on endpoint views and dynamic filters | |||||||
| Ability to schedule and perform tasks on endpoint views | |||||||
| Ability to assign preconfigured roles to console users | |||||||
| Ability to assign custom permissions to console users | |||||||
| User activity auditing | |||||||
| Installation via MSI packages, download URLs, and emails sent to end users | |||||||
| On-demand and scheduled reports at different levels and with multiple granularity options | |||||||
| Security KPIs and management dashboards | |||||||
| System status reports at different levels and with multiple granularity options | |||||||
| Device inventory and audits | |||||||
| Agent and agentless monitoring of devices | |||||||
| Patch management | |||||||
| Centralized software installation | |||||||
| Non-disruptive remote access | |||||||
| Remote Desktop | |||||||
| Built-in chat | |||||||
| Task automation and scripting | |||||||
| Component store - ComStore | |||||||
| Ticketing/Help Desk | |||||||
| Modules | |||||||
| Panda Data Control integration | |||||||
| Advanced Reporting Tool integration | |||||||
| SIEM integration | |||||||
| Panda Patch Management | |||||||
| Panda Full Encryption inregration | |||||||
| High availability service | |||||||
| Host platform certifications | ISO27001, SAS 70 ISO27001, SAS 70 | ISO27001, FISMA, SAS70, PCI DSS | |||||
| Supported operating systems | |||||||
| Supports Windows | |||||||
| Suppots Exchange | |||||||
| Supports macOS X | |||||||
| Supports Linux | |||||||
| Supports Android | |||||||
| Supports iOS | |||||||
| Support for virtual environments - persistent and non-persistent (VDI)** | |||||||
* Panda Fusion is a bundle of Panda Endpoint Protection Plus and Panda Systems Management. Panda Fusion 360 is the combination of Panda Systems Management and Panda Adaptive Defense 360 that are sold separately
** Compatible systems with the following types of virtual machines: VMWare Desktop, VMware Server, VMware ESX, VMware ESXi, Citrix XenDesktop, XenApp, XenServer, MS Virtual Desktop y MS Virtual Servers. Panda Adaptive Defense 360 & Panda Fusion 360 solutions are compatible with Citrix Virtual Apps, Citrix Desktops 1906 & Citrix Workspace App for Windows, Panda Securtity has been verified as Citrix Ready partner.
1* 100% Classification Service.
2* Threat Hunting and Investigation Service
Documentation:
Download the Panda Systems Management Datasheet (.PDF)

